Introduction
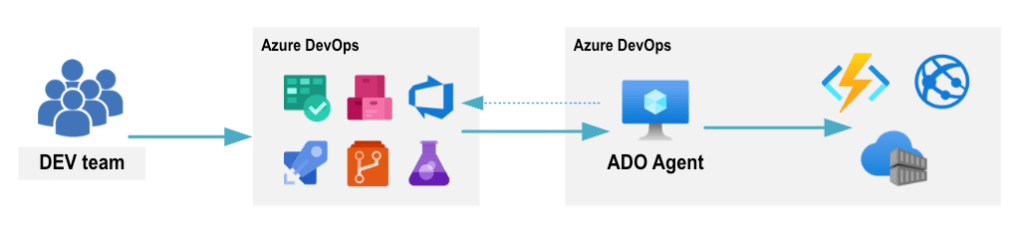
In modern cloud environments, securing the DevOps pipeline is crucial to protect sensitive data and ensure the integrity of deployments. Utilizing a self-hosted agent with Azure Key Vault provides an effective way to enhance the security of your DevOps processes. This architecture pattern integrates secure storage of secrets and credentials with robust deployment automation, ensuring that your applications and infrastructure remain secure and compliant.
When to Use This Pattern
You should consider using this pattern if:
- You need to manage and secure sensitive information such as passwords, API keys, and certificates.
- You require a high level of control over the build and deployment environment.
- Your organization mandates the use of on-premises resources for certain DevOps tasks.
- You are looking to improve the security posture of your CI/CD pipelines by avoiding public agents.
- You need to ensure compliance with regulatory standards by using managed identities and secure vaults.
Components and Roles
Azure DevOps Provides the platform for CI/CD pipelines and integrates with various Azure services.Manages build and release pipelines, integrates with version control systems, and automates deployments.
Self-Hosted Agent Executes CI/CD pipeline tasks within a controlled environment. Runs build and deployment tasks, interacts with local resources, and ensures compliance with security policies.
Azure Key Vault Stores and manages sensitive information securely. Provides secure access to secrets, certificates, and keys, integrates with Azure Active Directory for authentication, and supports managed identities.
Managed Identity Provides identity for applications to access Azure resources securely. Eliminates the need for hard-coded credentials, integrates with Azure AD, and simplifies identity management.
Security
Identity and Access Management
- Managed Identities: Use managed identities to securely access Azure Key Vault without storing credentials in the code.
- Role-Based Access Control (RBAC): Implement RBAC to restrict access to Azure resources, ensuring that only authorized users and services can access sensitive information.
Secret Management
- Azure Key Vault: Store all sensitive information such as passwords, API keys, and certificates in Azure Key Vault.
- Access Policies: Define and enforce access policies to control which users and applications can retrieve secrets from the Key Vault.
Network Security
- Virtual Network (VNet): Integrate self-hosted agents with Azure Virtual Network to isolate build and deployment environments from the public internet.
- Private Endpoints: Use private endpoints to securely connect to Azure Key Vault and other Azure services, ensuring that traffic remains within the Azure backbone network.
Scalability
Self-Hosted Agents
- Horizontal Scaling: Add more self-hosted agents to handle increased load, ensuring that build and deployment tasks can be executed concurrently without delays.
- Dynamic Scaling: Implement dynamic scaling strategies to automatically start or stop self-hosted agents based on the workload.
Azure Key Vault
- Throttling: Monitor and manage the rate of requests to Azure Key Vault to avoid hitting service limits.
- Replication: Use Key Vault replication features to ensure high availability and redundancy across different regions.
Availability
High Availability
- Self-Hosted Agents: Deploy self-hosted agents across multiple regions and availability zones to ensure high availability and fault tolerance.
- Azure Key Vault: Leverage Azure Key Vault’s built-in high availability features and configure geographic redundancy to protect against regional outages.
- Backup and Restore: Regularly back up the Azure Key Vault and other critical resources to enable quick recovery in case of data loss or corruption.
Network
Network Configuration
- Virtual Network (VNet): Configure VNets to securely isolate self-hosted agents and Azure Key Vault from public access.
- Network Security Groups (NSGs): Use NSGs to define and enforce security rules that control inbound and outbound traffic to the VNets.
- Service Endpoints: Utilize service endpoints to allow secure access to Azure services like Key Vault from within the VNet.
Network Flow
- Pipeline Execution: CI/CD pipelines are triggered in Azure DevOps.
- Self-Hosted Agent Execution: Tasks are executed on self-hosted agents, which are connected to a VNet.
- Secret Retrieval: The self-hosted agent retrieves secrets from Azure Key Vault using managed identities.
- Deployment: The self-hosted agent deploys the application or infrastructure components to Azure or on-premises environments.
By following these guidelines, you can establish a secure DevOps deployment process using a self-hosted agent and Azure Key Vault, ensuring that your sensitive data is protected and your deployment pipelines are robust and compliant. For more details or specific inquiries, feel free to contact us or leave a comment.
Laisser un commentaire